Hacking Your Home Pen Testing Your Local Network By Aliaksandra Havia Medium How To Perform A Successful Wifi Penetration Test Ultimate Guide On How To Perform A Successful Network Penetration Test How To Set Up A Pentesting Lab Rapid7 Blog Share this post. Step 2 of this network penetration testing checklist involves using this information to run tests on the target system scouting for obvious vulnerabilities.
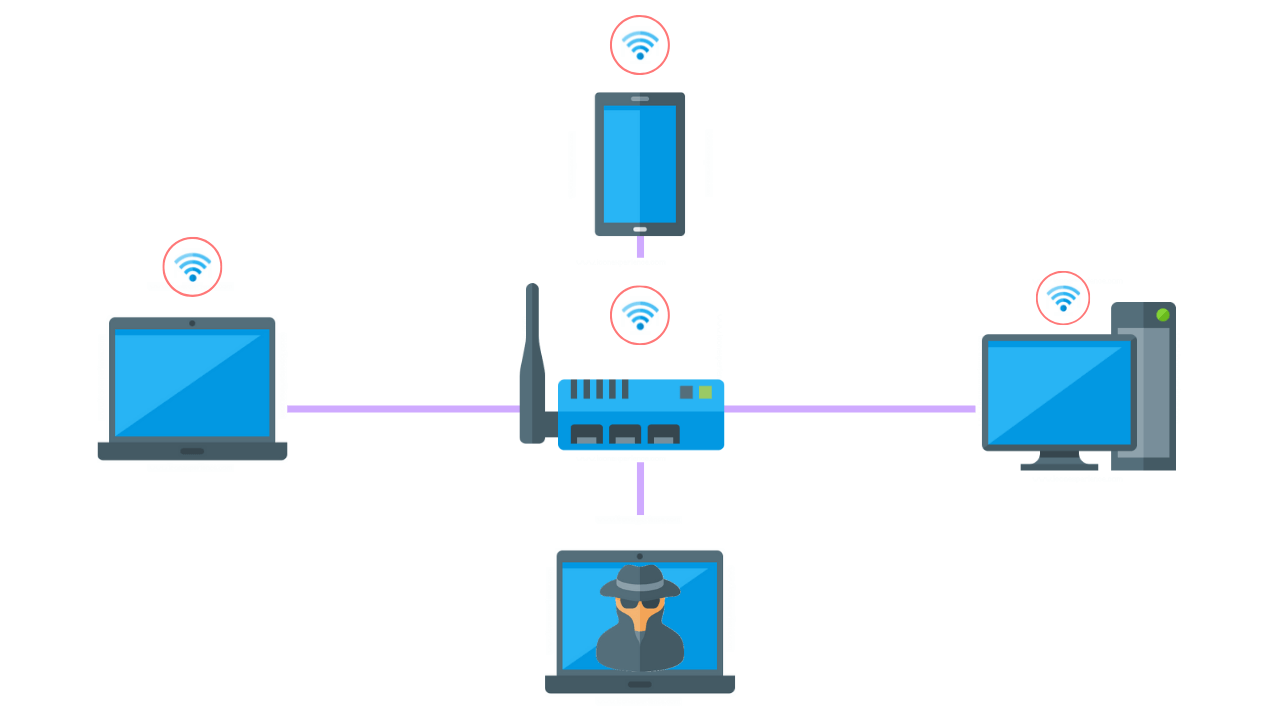
How To Perform A Successful Wifi Penetration Test
Disable the Windows Firewall.
. 9 level 1 2y Call your cell phone and see if they give you passwords. Some of the tools that can support us with this step are. Ii Configure the exploit with remote IP address and remote port number.
Most people have zero need for an XP VM in their home network since most people dont have industrial systems at home. Disable the Windows Firewall. TCP Scanner ports 1-65535 2.
After collecting all the information you can about your target network its time to use this information for something dicey. Click on the Windows icon in the far left of your taskbar followed by Settings the cog symbol that appears just above it. All the communication between trusted and untrusted zone flow through firewall and it grants or reject the access.
Expect to find only the ports you know you have explicitly opened open. The first thing they are going to do is port scan your IP address and find out what youve got running if anything. Advanced IP Scanner is one of the programs that undoubtedly supports this fundamental step of Network PenTesting.
When you first plug the device in and open the lid it creates a new WiFi network. While youre examining your network traffic you should look for Link-Local Multicast Name Resolution LLMNR and ensure that its disabled if possible. When it comes to a WIFI Pentesting its important to understand what networks are being used or related to the business youre targeting.
To do this open a port on your router and rerun the scan. Low-cost Pentest Lab in 2021. The Lovebox has an interesting way of accomplishing this.
First run a full scan against your home IP address. Weidman said that you can capture password. 1 level 1 2y Spin up a VPS somewhere and use nmap to do a port scan to make sure everything is block.
To connect the network you must type the username and click connect. Scroll down and click Update Security to open the menu. The first thing we need to do is connect the box to a WiFi network.
The next step is the vulnerability scan it allows to identify any type of hole within the operating system of the chosen target. Planning and reconnaissance The first stage involves. It can be implemented between trusted zone Corporate Network Area and untrusted zone Internet.
The first step of every Pentesting is reconnaissance in which we have to gather as much information as possible to understand our target even better. First run a full scan against your home IP address. Below we have explained how to ensure it is turned on.
I Pick which exploit to use. GIFLanguard Nessus Ratina CS and SAINT. To do this open a port on your router and rerun the scan.
If you try to perform pen test on the public IP then ASA being a security device will block the attacks. Penetration testing also known as pen testing is a simple term that means you are looking at your computer system to determine if it has any security vulnerabilities that could be. Or you can extend the Wired network by running cables into other rooms or using your power cables by installing home plug adapters.
If youre not running anything and all ports are closed the attack is basically done unless there is a super critical known vulnerability unpatched on your edge router the chances of getting in with no ports open is extremely low. Live data can be read from Ethernet IEEE 80211 PPP HDLC ATM Bluetooth. However should you want to pentest these areas you would need to obtain explicit permission from the end user to inventory classify and perform a risk analysis on the networks supporting their home-based environment.
For the beginning pentester a pentesting lab only needs to include a vulnerable target computer and a pentesting computer. Advanced IP Scanner is one of the programs that undoubtedly supports this fundamental step of Network PenTesting. A targeted pentest is one of the best ways to ensure all network compliance requirements are being met.
With emphasis on Nessus this tool allows us to obtain the following information. Ad Een pentest geeft u inzicht in de beveiligingsrisicos van uw bedrijf. To connect the network you must type the username and click connect.
The first thing they are going to do is port scan your IP address and find out what youve got running if anything. Expect everything else to be filtered. How to pen test a firewall externally Firewall is a device or software which is responsible for filtering traffic of network.
Now click on Windows Security in the menu on the left. OpenVAS TCP Full Scan ports 1-65535 4. Get instant access to custom vulnerability scanners and automation.
However as skill levels and the need for realism increase the number and complexity of the targets will need to grow and more components will be added to the target network. 0 Response to how to pentest your home network Post a Comment. UDP Scanner top 1000 ports 3.
Ii Configure the exploit with remote IP address and remote port number. First run a full scan against your home IP address. Step 1 -Open your terminal.
UDP Scanner top 1000 ports 3. To connect the network you must type the username and click connect. Tips on how to secure your home network from hackers.
Ii Configure the exploit with remote IP address and remote port number. The next is Wireshark a network protocol and packet analyzer that is important when it comes to penetration test tools. Then verify that it is your home router that is performing the filtering and not your ISP.
Building A Test Lab For Pentesting Guide White Oak Security
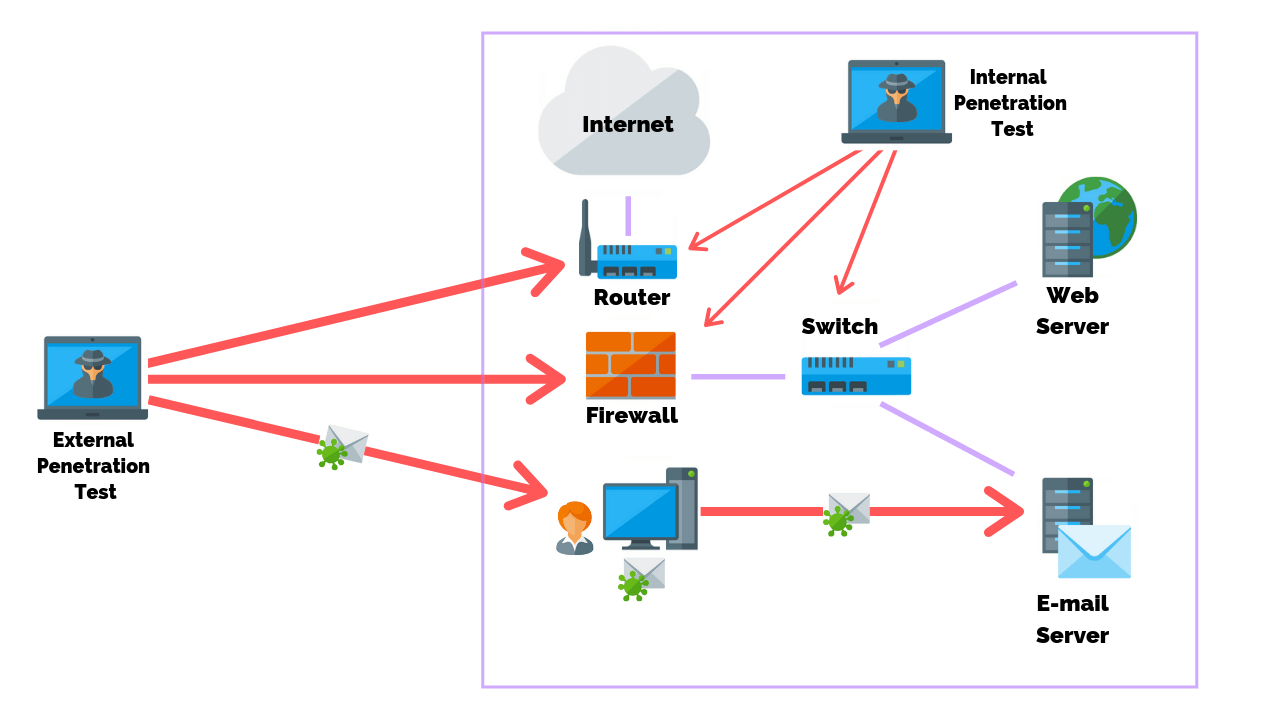
Firewall Penetration Testing Steps Methods Tools Purplesec
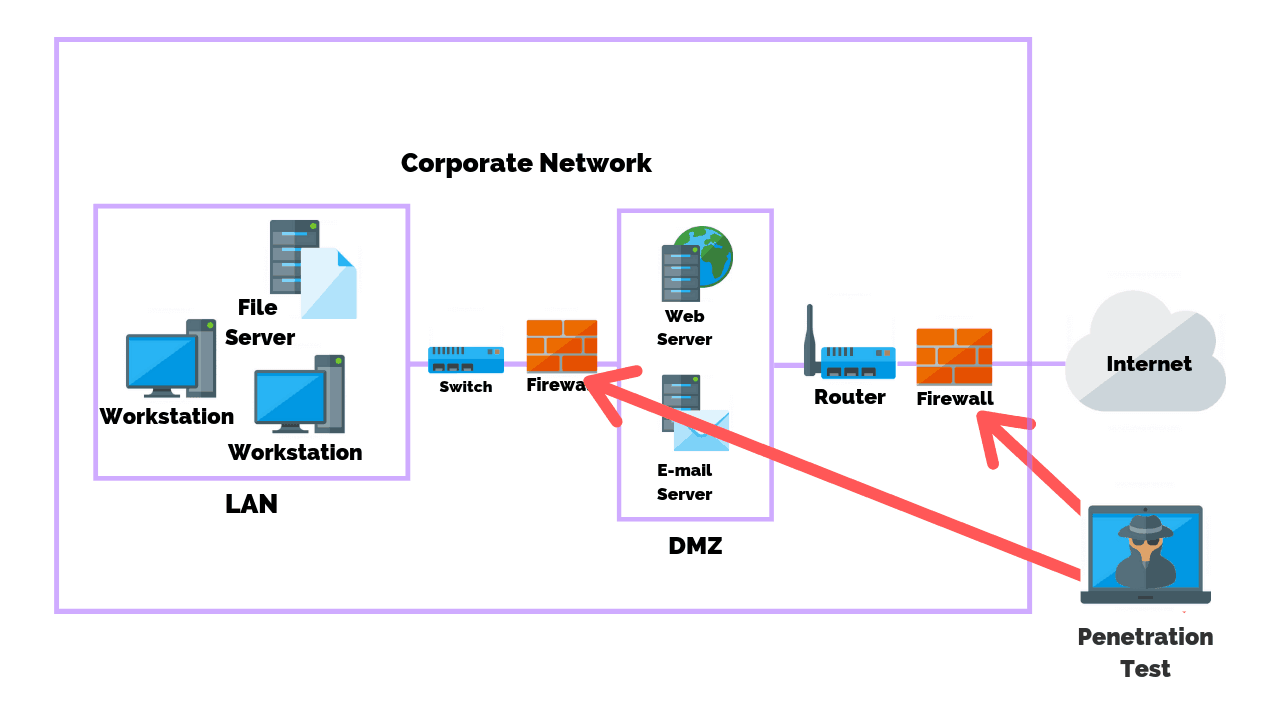
Firewall Penetration Testing Steps Methods Tools Purplesec
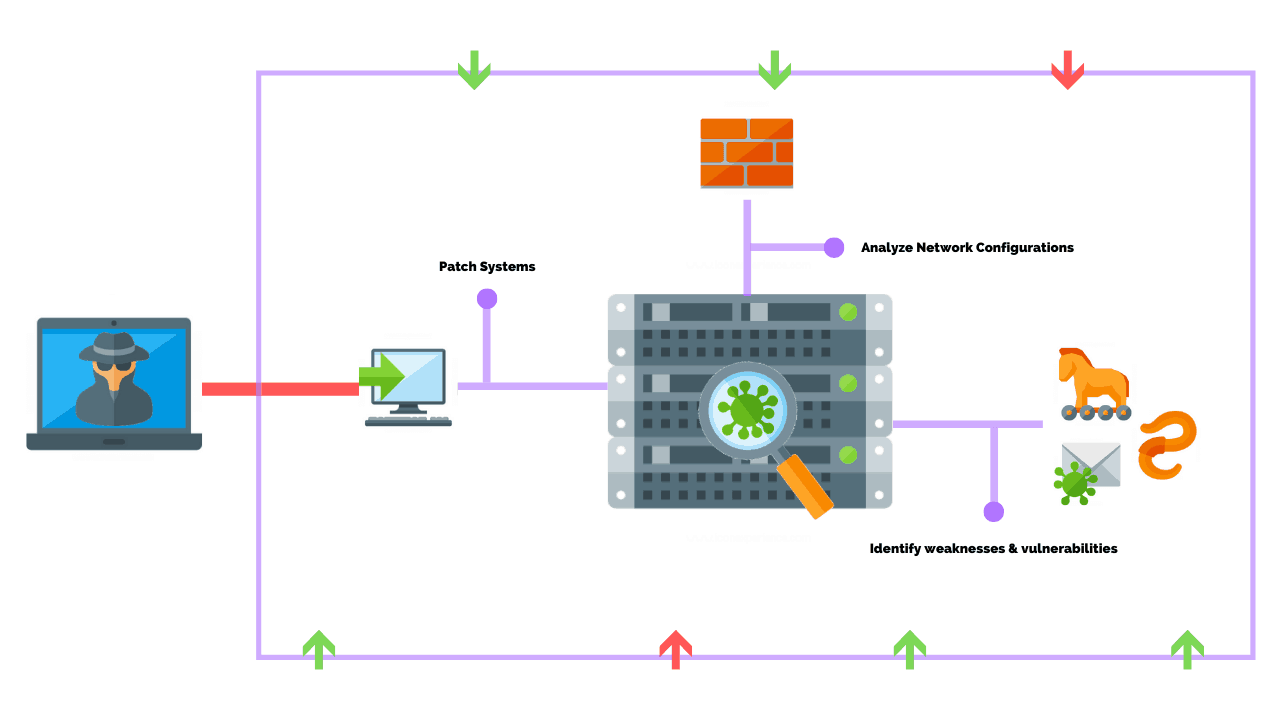
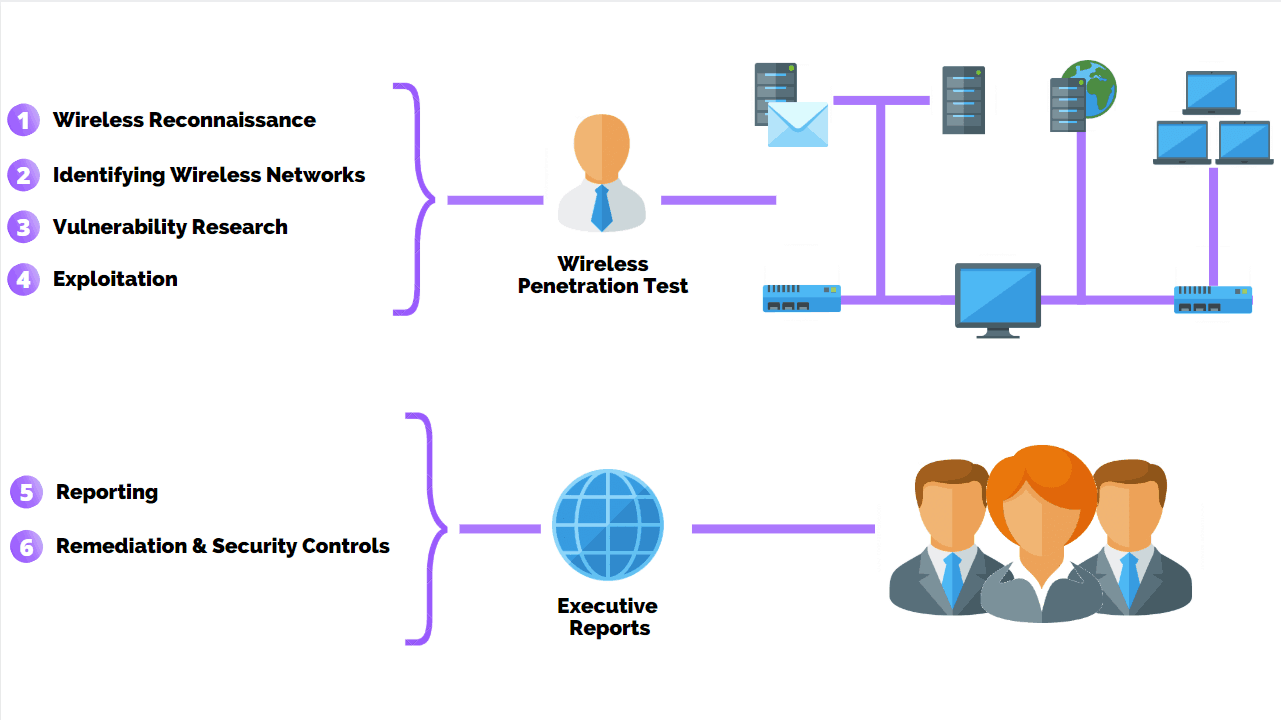
How To Perform A Successful Network Penetration Test Purplesec

How To Perform A Successful Wifi Penetration Test

Penetration Testing Complete Guide With Penetration Testing Sample Test Cases


0 comments
Post a Comment